This week cybercrime has taken an unprecedented backseat to physical crime! The famous Louvre Museum in Paris gets robbed and the mafia has leapt back onto the scene in two shocking, and related stories where NBA basketball, the mafia and poker collide!
Before we get to it, I have a favor to ask. If you’ve read my new book Spies, Lies, and Cybercrime, or listened to the audible version (with me reading it!) please leave me a review on Amazon. The more reviews, the more Amazon pushed the book before the eyes (and hopefully into the hands) of other future spy hunters.
Title Story: A four-minute masterpiece of precision and nerve, as thieves slip into the Louvre in daylight and vanish with $102 million in royal jewels.
Cybersecurity Tip of the Week: The surest way to stop a thief isn’t with firewalls or cameras—it’s knowing your data well enough to spot when someone’s misusing it.
Crime of the Week: The FBI just busted a nationwide sports-betting and poker racket tying NBA stars to old-school mob families.
SpyCraft Insight: From Paris to the NBA, every successful crime—and every spy mission—runs on one thing: privileged information.
Appearances of the Week: I discuss the CIA in Venezuela, the AWS glitch, tips and and tricks to protect yourself and your family, all while on the road promoting Spies, Lies, and Cybercrime.
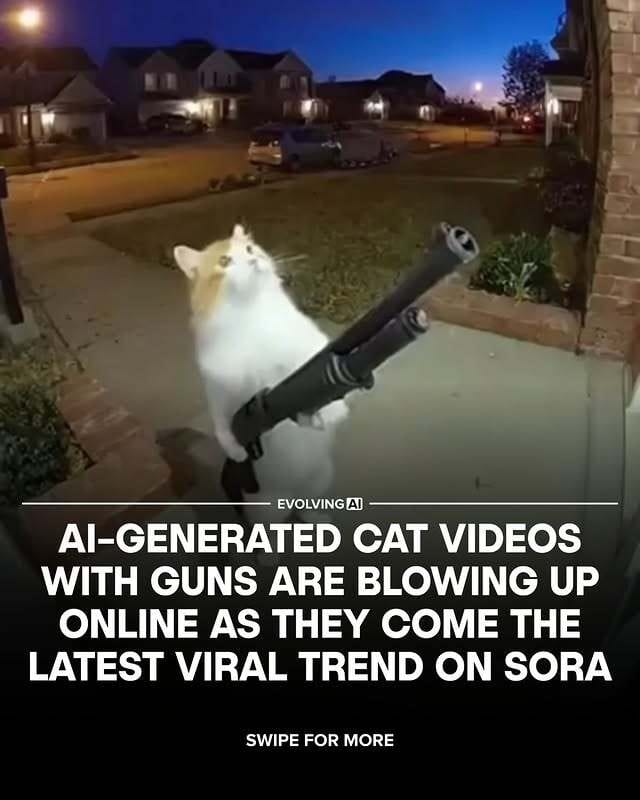
AI Trend Of the Week: Cats. With Guns?!
Title Story
The Paris Heist, the Mafia’s Comeback, and the Return of the Old World Criminal

Early Sunday morning on October 19, 2025, the doors of the Louvre Museum opened to the public as usual. By around 9:30 a.m., in the stepped halls beneath the glass pyramid, a small team of four intruders struck. They arrived mounted on a basket-lift truck parked outside the Seine façade, climbed into the air, forced a window on the second floor, and entered the gallery that holds France’s remaining crown jewels: the ornate Galerie d’Apollon.

Map courtesy of the BBC.
Inside, guards were threatened and forced to evacuate. Within minutes, sparks flew as the thieves sliced through two display cases, grabbed eight royal artifacts—including a diamond bow once worn by Empress Eugénie—and fled. By 9:38, they were gone, weaving into Paris traffic on two scooters, their $102 million haul hidden under tool bags.
The Louvre’s director later told French senators that the only exterior camera facing the wall had been angled away, leaving the balcony and window unmonitored. A third of the rooms in that section had no CCTV at all. The heist lasted four minutes in a museum famous for security.
Investigators say the criminals were undeterred by the presence of guards and tourists. They neither used guns nor caused visible bloodshed. Instead, they relied on speed, stealth, and structural access from below—parking the lift, climbing into the gallery early, and slipping out before full security could mobilize.
Police flooded Paris, collecting DNA, fingerprints, and security footage from nearby streets. One week later, investigators made their first arrests: two men known for jewelry theft, one caught at Charles de Gaulle Airport as he tried to flee the country. Their DNA matched samples lifted from the scene. Both are now in custody, and the hunt for their partners (and the missing jewels) continues.
The backdrop adds weight: much of France’s royal-jewel collection was lost during the Revolution, and surviving pieces were auctioned off in the 19th century, bought in large part by an American jewel magnate. These eight objects were among the last remaining physical links to a monarchy that France renounced—and now they’re stolen again. Security at the Louvre is now under scrutiny.

A crown worn by French Empress Eugénie was targeted by thieves during a heist at Paris’ Louvre Museum on October 19, but was dropped during their escape.

A jewel-encrusted brooch worn by French Empress Eugénie.

A tiara adorned with pearls worn by French Empress Eugénie.

The Crown Jewels.
The thieves’ choices suggest careful reconnaissance. They picked the gallery where the priceless jewels were on display, timed the entry just after opening, used external access from a construction façade, and left behind tools and the lift truck that still bear forensic marks.
The Louvre reopened its doors, but the Galerie d’Apollon remains sealed. The jewels, relics of kings and emperors, have vanished. Not to war or revolution, but to precision, timing, and someone who knew exactly where the cameras didn’t look.
Cybersecurity Tip of the Week
How to Spot a Trusted Insider
Every great heist begins with trust. The Louvre thieves may have slipped in through a second-floor window, but it’s likely that someone opened a different kind of door for them. Maybe it was a contractor who knew that the cameras weren’t watching that street. Maybe a staff member shared the security protocols and response time for an armed theft. However it happened, they exploited what every spy and every cybercriminal knows: it’s easier to be invited in than to break in.

The same rule applies in cybersecurity. Most breaches don’t start with a hacker in a hoodie; they start with an insider—an employee, contractor, or partner—who already has access. Sometimes the betrayal is intentional: a disgruntled worker, a spy, or someone offered money by a competitor or foreign actor. More often, it’s unintentional: a person tricked by social engineering, spear-phishing, or simple curiosity.
Insiders leave traces before they leave the building. Watch for the patterns that don’t fit. An employee suddenly working odd hours, accessing systems they normally wouldn’t. Someone downloading large amounts of data “for backup.” Staff who grow defensive when questioned about projects or who seem unreasonably curious about unrelated information. Even small anomalies—a USB drive that keeps reappearing on desks, a badge scan after hours—should trigger a quiet review, not a shrug. Most importantly, build a culture where people aren’t afraid to speak up. Insiders thrive in silence.
The Louvre’s jewels were protected by glass, sensors, and guards. None of it mattered if someone inside shared the map. The same is true in every company that treats cybersecurity as a technology problem instead of a people problem. Spies don’t breach firewalls, they exploit trust.
Crime of the Week
The Mafia Makes a Comeback
Cybercrime has dominated headlines for years—but this week, old-school organized crime muscled its way back into the spotlight. In an FBI sting stretching across 11 states, over 30 people were arrested, including Miami Heat guard Terry Rozier and Portland Trail Blazers head coach Chauncey Billups.

The charges: wire fraud, money laundering, extortion, and illegal gambling. Also, a link to the mafia: the Bonanno, Gambino, Genovese, and Lucchese families.
According to the DOJ, two intertwined conspiracies emerged. The first was a sports-betting scheme exploiting insider NBA information. Players would allegedly sit, feign injury, or exit early, allowing insiders to “bet the under” and make a small fortune. The second was a high-tech poker operation where former NBA players (A.K.A. mob-backed “Face Cards”) would entice wealthy VIPS into rigged games of Poker. Unbeknownst to the “Fish,” everyone at the table, including the NGA celebrity and the dealer was in on the scam. They even used wireless cheating devices and Xray machines to rig the game.
The FBI called it “one of the most brazen sports corruption cases since sports betting became legal.”
It’s a reminder that while ransomware may rule the digital world, the analog crooks never retired—they just waited for the odds to swing their way. When sports, tech, and the mob overlap, the house doesn’t win. The house is complicit.
Cybersecurity Tip of the Week
SpyCraft Insight
Every crime in this issue, from Paris to Portland, turns on one truth: information pays. The Louvre thieves knew the museum’s blind spots. The mafia knew which athletes to reach and how to hook VIP “fishes” with athletes in their pocket. In both cases, the advantage was knowledge, not strength or skill. Spies, hackers, and hustlers all live by the same rule: whoever controls the information controls the outcome.

To turn the tables we need to think like the spies and criminals that seek to deceive us so that we can recognize the threat and respond like Spy Hunters. This begins with knowledge of our own that takes the playbook from the adversary and allows us to know their moves before they make them. Fortunately, there’s a bestselling book for that!
Thanks to all of you, my book, Spies, Lies, and Cybercrime, is an instant national bestseller and an Amazon #1 Bestseller.
f you haven’t already, please buy SPIES, LIES, AND CYBERCRIME. If you already have, thank you, and please consider gifting some to friends and colleagues. It makes a perfect holiday gift for anyone you want to protect from cyber scams.
Leave a 5-star review on Amazon. Reviews are the secret weapon that triggers Amazon’s algorithm to share the book with thousands of new readers who might not otherwise find it — and might otherwise fall prey to an attack.
Please share! Forward this email to your friends and family. Here's an easy-to-post cover graphic, here's a Linkedin post, here's an IG reel and a post.
Want a SIGNED COPY? Get one here.
Have you ordered a copy of Spies, Lies, and Cybercrime (book, kindle or audible)?
Appearances of the Week
I’ve been busy promoting Spies, Lies, and Cybercrime and informing viewers and readers everywhere to be careful of online threats and the upcoming holiday scams.
Here I am in a Forbes interview discussing the AWS outage that caused mayhem across the internet.
Here I am on NTD News and Fox 32 Chicago speaking about Spies, Lies, and Cybercrime and tips to protect yourself and your family from cybercriminals.
And finally, in an Interview with the New York Post talking about what the CIA’s covert operations in Venezuela might mean.
AI Trend of the Week
Cats. With guns.
It’s the latest AI fever dream—hyper-realistic, cinematic felines armed to the teeth, spreading from Sora to TikTok and Instagram like digital wildfire.
AI keeps blurring the line between creativity and absurdity. So, what do you think—brilliant satire, or the moment we officially lost the plot?
Realtime User Onboarding, Zero Engineering
Quarterzip delivers realtime, AI-led onboarding for every user with zero engineering effort.
✨ Dynamic Voice guides users in the moment
✨ Picture-in-Picture stay visible across your site and others
✨ Guardrails keep things accurate with smooth handoffs if needed
No code. No engineering. Just onboarding that adapts as you grow.
Praise for Spies, Lies, and Cybercrime!

"O’Neill deftly attests [that] taking proper precautions can limit, if not halt, the damage wrought by unscrupulous cybercriminals. His masterful book serves as an important guide for individuals and companies committed to avoiding an epic misstep." — Booklist
“One breach can sink a business—or a billion-dollar idea.” —Marc Randolph, Co-Founder and First CEO of Netflix
“A chilling and essential wake-up call that reads like a thriller, but every word is terrifyingly real.” –Brad Thor, #1 New York Times bestselling author of Edge of Honor
Order Spies, Lies, and Cybercrime
I hope you love the book as much as I loved writing it for you! Please leave a review. Great reviews help others find the book.
📚 Get the book: https://ericoneill.net/books/spies_and_lies/
📺 Review the Book: https://www.amazon.com/Spies-Lies-Cybercrime-Cybersecurity-Outsmart/dp/0063398176/
🎤 Book me to speak at your next event: https://www.bigspeak.com/speakers/eric-oneill
Like What You're Reading?
Don’t miss a newsletter! Subscribe to Spies, Lies & Cybercrime for our top espionage, cybercrime and security stories delivered right to your inbox. Always weekly, never intrusive, totally secure.
Let's make sure my emails land straight in your inbox.
Gmail users: Move this email to your primary inbox
On your phone? Hit the 3 dots at top right corner, click "Move to" then "Primary."
On desktop? Close this email then drag and drop this email into the "Primary" tab near the top left of your screen
Apple mail users: Tap on our email address at the top of this email (next to "From:" on mobile) and click “Add to VIPs”
For everyone else: follow these instructions