In This Issue
Title Story: Classification in the Age of Oops - A deep dive into the Signal scandal written by a former FBI intelligence officer (your truly).
Cybersecurity Tip of the Week: Don’t be like US Government Officials. Lock down your payment applications!
Cybersecurity Breach of the Week: The attack on Oracle and the loss of medical records is being investigated by the FBI. The attackers are seeking to extort medical providers.
Tech of the Week: ChatGPT’s new image generator is mind blowing!
Appearance of the Week: Eric sits down with the Secrets & Spies Podcast.
Title Story - OPERATION BROKEN SIGNAL: CLASSIFICATION IN THE AGE OF OOPS

It All Began with a Signal “Glitch”
Picture this: You’re a journalist, minding your own business, when your phone buzzes with a message request on the end-to-end encrypted app Signal. The sender claims to be Mike Waltz, President Trump’s National Security Advisor. Odd, right? But you accept—curiosity is part of your job—and suddenly find yourself in a group chat labeled “Houthi PC Small Group,” populated by senior administration officials. As you scroll through the messages, it dawns on you that they’re discussing imminent military strikes against Houthi rebels in Yemen, mapping out launch times, drone deployments, and targeted buildings.
That’s exactly what happened to Jeffrey Goldberg, the editor-in-chief of The Atlantic. At first, he claims to have assumed it was some bizarre prank or a foreign intelligence trap. After all, how likely is it that actual high-level officials would talk attacks on an app they share with a journalist? But over the next few days, the timetables in these messages aligned perfectly with real-world airstrikes. Skepticism gave way to certainty: The national security leadership of the United States was coordinating a lethal operation on a public messaging platform—and had inadvertently included a major reporter. Welcome to Operation Broken Signal, where one accidental chat invite laid bare a fundamental truth: convenience too often trumps security, even at the highest echelons of power.
The Nuts and Bolts of the Yemen Strike Details
Inside the chat, Secretary of Defense Pete Hegseth posted information specific enough for a Hollywood action movie script. Weather checks were called favorable, F-18 fighter jets were queued for launch, and exact times for bombs to drop were spelled out in black and white. At one point, the messages revealed plans for sea-based Tomahawk missiles to fly at 3:36 p.m. Eastern Time, and Hegseth even noted which “top terrorist” was being tracked in real time.

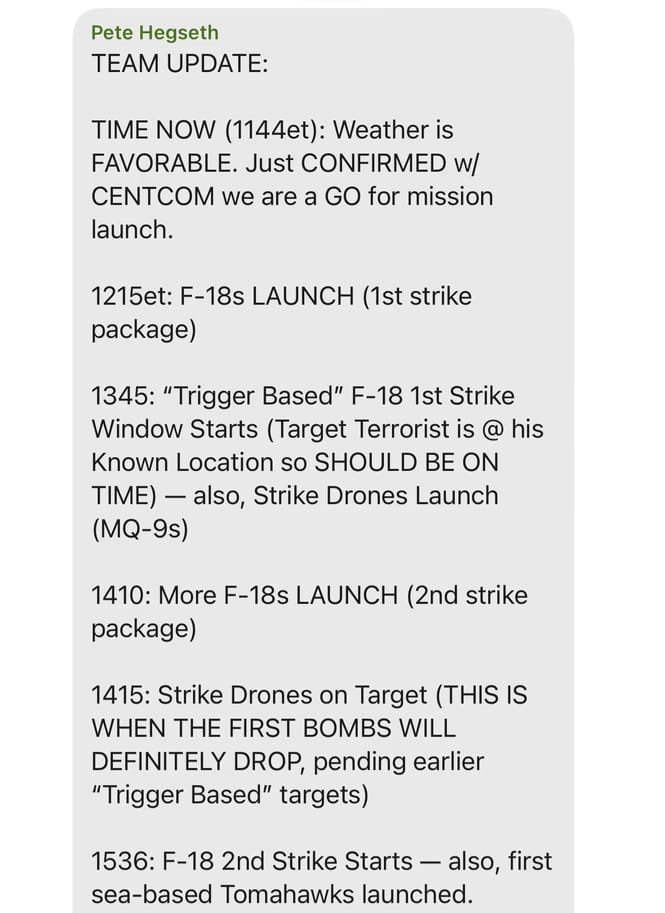


From a military standpoint, sharing real-time strike schedules and target information on an unsecure channel is deeply concerning. Had this data fallen into the Houthis’ hands—even just a couple of hours before the operation—they could have fortified defenses, evacuated key leaders, or ambushed U.S. pilots. It’s the type of info that is typically restricted to a Sensitive Compartmented Information Facility (SCIF) or at least a locked-down government system where officials know exactly who’s in the conversation. Yet in this instance, they were effectively brainstorming a sensitive attack over a consumer app, unaware that a journalist was reading along.
The operation itself, from a purely military perspective, was a success. Targets were hit, missiles found their mark, and the strike was a win for America’s “peace through strength” approach. Only later, after the bombs had fallen, did anyone realize that Goldberg had received live updates on each step of the assault.
Was It Classified—Or Not?
Publicly, White House officials, including Defense Secretary Hegseth, CIA Director John Ratcliffe, and Director of National Intelligence Tulsi Gabbard, insisted the conversation was “sensitive” but not “officially classified.” Under U.S. law, the Secretary of Defense has the power to decide classification levels, so if Hegseth declared it “unclassified,” there may be a tidy legal firewall against accusations of wrongdoing.
However, many outside voices cried foul. Military and intelligence experts scoffed at the idea that a blow-by-blow attack plan was somehow unclassified. A retired senior commander flatly stated that until the strike is over, such details are “absolutely classified” because the lives of American pilots depend on secrecy. I can honestly say that when I operated undercover, investigating the top spies and terrorists in the United States, any communication outside of our secure channels would have gotten me in hot water at best, and possibly arrested.
Complicating matters further, the Biden administration’s Cybersecurity and Infrastructure Security Agency (CISA) explicitly endorsed Signal in 2024 as a “best practice” for highly targeted government officials. Amid mounting concerns over Chinese-linked cyber threats, CISA hailed apps with end-to-end encryption—especially those offering disappearing messages—as key to fending off hostile actors. By prioritizing strict protocols, Signal was positioned as a valid security measure for officials seeking safe digital communication. The real question, then, isn’t whether Signal can be secure, but rather if it was prudent—or ethical—to discuss attack plans on any platform that made it so easy to mis-add participants.
This disconnect between the official stance and common sense reveals a larger quirk of government classification. By calling something “not classified,” high-level leaders can arguably shield themselves from legal ramifications. Of course, that doesn’t address whether it was reckless or unethical to hold war councils on an app known for ephemeral messages and easy user mix-ups. But from a purely legal vantage, proclaiming “it’s not classified” is a get-out-of-jail-free card—at least for the moment.
Goldberg’s Role
Jeffrey Goldberg’s behavior in this episode has attracted criticism. Rather than immediately declaring, “Hey, guys, wrong person,” he lingered in the chat for days, gathering more details. Critics suspect he was biding his time, waiting for the juiciest scoop that would embarrass President Trump’s team. Goldberg, on the other hand, insists he stayed because he was unsure of the chat’s legitimacy. He worried it might be a prank or a disinformation campaign, so he consulted colleagues and his lawyers, verifying details until he finally realized it was all real. Then he ghosted the chat.

Jeffrey Goldberg speaks on stage in Washington, D.C. (The Atlantic)
Either way, Goldberg walked away with a massive story, published the chat logs (minus one redacted CIA officer name), and promptly triggered a media storm over whether top officials were playing fast and loose with national security. Legally, he appears to be in the clear. Journalists have broad protections when receiving unsolicited info. Yet ethically, the question remains: Should he have alerted authorities sooner if he truly believed he was witnessing a serious breach? Goldberg’s defenders say it’s not a journalist’s responsibility to fix officials’ mistakes—only to report them. His detractors argue he continued to listen in on what he claimed was classified information, effectively letting the situation unfold for personal gain. The truth likely sits somewhere in-between.
Why No One Is Going to Jail
In a perfect world, you'd expect a major security scandal to yield consequences for those who shared operational details on a non-secure platform. But in the real United States, it’s become abundantly clear that high-level officials often evade accountability for mishandling sensitive information. The outrages keep accumulating, yet prosecutions remain elusive.

National security advisor Mike Waltz and Secretary of Defense Pete Hegseth at the White House on Feb. 24. (Reuters)
Part of the reason is cultural apathy toward classification rules. The country has witnessed revelations of former presidents keeping classified documents in private bathrooms, garages, or locked file cabinets. Trump kept boxes of confidential files in a Mar-a-Lago storage room, while Biden stashed boxes of classified material next to a vintage sports car in his Delaware home. When Secretary of State Hillary Clinton used a private email server for official correspondence, she faced a firestorm of criticism—but no formal indictment. Federal agencies discovered that 100 of her emails contained information that should have been deemed classified at the time, including 65 marked “Secret” and 22 deemed “Top Secret.” Another 2,093 were retroactively designated confidential. Critics hammered her for the breach, claiming it exposed national security secrets to hackers. Yet, despite widespread anger, Clinton was never prosecuted.
This track record of non-prosecution at the highest level—spanning Republicans and Democrats alike—suggests a pattern: we talk about the sanctity of classified material, but we rarely punish those who trample those rules. Whether it’s email servers in private bathrooms or army squads planning attacks in group chats, the end result is often a stern talking-to, at most. Meanwhile, average federal employees can face termination or even prison for far smaller lapses.
Given all this, it seems downright predictable that no one in the “Houthi PC Small Group” will face serious consequences. The “no classification, no crime” defense (and the successful strike in Yemen) covers the administration’s flank. Jeffrey Goldberg, for his part, may get some critics fuming about his methods, but it’s unlikely he’ll be dragged into court for simply being added to a chat. In the end, it’s a storm in the news cycle that might fade without lasting repercussions.
Bigger Implications: Convenience vs. Security
Operation Broken Signal underscores the perennial tug-of-war between convenience and security. If you’re an official with a frantic schedule, hopping on a consumer app is so much easier than schlepping to a secure facility, opening an encrypted laptop, and toggling the “classified” switch for every sentence. But in the world of cybersecurity, that convenience lulls even the savviest officials into massive oversights. One accidental invite or wrong contact, and your attack plan is in the hands of someone who absolutely should not have it.
It’s a broader cautionary tale that resonates far beyond government. Regular people inadvertently leak sensitive information all the time—through misdirected emails, “reply-all” debacles, or hasty Slack messages. Company data can be exposed, personal data sold or stolen, and reputations tarnished. Human error is a top cause of data breaches in the private sector, and the same dynamic plays out at the highest levels of national security. If leaders of a superpower can botch a group chat, is it any wonder the average employee can too?
The moral is simple: operational security requires vigilance and, yes, a bit of inconvenience. That could be the difference between a well-guarded plan and a fiasco that ends up fueling prime-time headlines. Convenience is the enemy of secrecy. The more we prioritize speed and ease, the more we gamble with our own—or our nation’s—confidential data.
Conclusion: A Lesson in Laxity
Operation Broken Signal began as a small “glitch,” but it unraveled into a larger commentary on American attitudes toward sensitive information. Whether it’s mislabeled chat messages or private email servers containing hundreds of documents stamped “Top Secret,” the thread running through these controversies is the same: we talk about the importance of classified data yet seldom see meaningful repercussions for those who violate established protocols. Convenience and complacency repeatedly trump security, from White House principals to everyday employees.
At the end of the day, no one in this saga is likely to be prosecuted. The White House swiftly brushed off accusations, claiming no official classification was assigned, and the Yemen strike itself went forward without issue. Jeffrey Goldberg’s slow departure from the chat may raise eyebrows, but his decision to document it all likely remains protected journalism. The entire drama serves as a reminder that humans, no matter their rank, are prone to careless oversights when it comes to handling precious information.
If we want stricter accountability, we need more than sporadic outrage. We need consistency in enforcing rules and a cultural shift that values caution over convenience. It’s easy to point fingers, but the next data breach—be it from a top official or a small-town entrepreneur—could be just one careless invite away. Operation Broken Signal might become a footnote in the broader saga of national security mishaps, but it leaves us with one unassailable truth: if even the national-security leadership of the world’s most powerful country can’t secure a chat, the rest of us need to double-check before we hit “send.”
Cybersecurity Tip of the Week
LOCK DOWN YOUR PAYMENT APPS
So here’s a story that’ll make you check your privacy settings right now.
After The Atlantic accidentally exposed a Signal chat involving Trump officials and U.S. attack plans in Yemen, several of those same officials did what any top-tier national security strategist would do in a panic…They scrambled to clean up their Venmo accounts.
Turns out, their contact lists were wide open—visible to anyone. Journalists, military officials, even members of Congress, all just sitting there for anyone with a free afternoon and a little curiosity. Mike Waltz, the White House national security adviser, had his contact list exposed until the day after the story dropped. Former Defense Secretary Pete Hegseth? Same. He deleted his account.
So here’s what YOU do:
Go to your Venmo settings. Set your activity to Private.
Do the same with Cash App, PayPal, Zelle, whatever you use.
And for the love of God, turn on Multi-Factor Authentication.
You don’t want a Russian spy—or your nosy neighbor—tracking your pizza purchases and late-night impulse buys. This stuff matters. In our online-first world, even a yard-sale couch payment can say more than you think. Keep it close. Keep it quiet.
And please—update your settings before someone else does it for you.
Cybersecurity Breach of the Week: Extorting Oracle
Oracle has confirmed a major data breach impacting patient records stored on legacy servers it inherited from its $28 billion acquisition of Cerner. Hackers infiltrated these outdated systems, copied sensitive health data, and launched extortion attempts against multiple U.S. medical providers. The stolen data—which had not yet been migrated to Oracle’s more secure cloud—includes personally identifiable health information. The breach was discovered in late February, and the FBI is actively investigating.
Why you should care: This wasn’t just data theft—it was weaponized blackmail. Health records can reveal deeply personal information: mental health diagnoses, addiction history, reproductive care, and more. Criminals can use this data to extort victims directly or pressure healthcare providers into silence and payout. Even worse, this attack targeted providers tied to government systems, including the Department of Veterans Affairs—raising national security implications. The lesson is clear: no company inherits just assets in a merger—they also inherit risks. Robust cybersecurity must be a top priority, especially when absorbing older systems with weaker defenses. [Special thanks to Hugh for sending me this breach].
Tech of the Week: ChatGPT’s New Image Generator Is a Game Changer
I’ve been testing ChatGPT’s new image generator, and let me tell you—it’s got a serious wow-factor. I’ve used a lot of image tools over the years, from the clunky to the clever, but this one? It’s like giving a DSLR and an art degree to an AI that actually listens.
The title image for this newsletter was generated through ChatGPT, and it took just one sentence. One. No back-and-forth. No confusing menus. No “almost there” results. Just clean, stunning visuals that look like they were taken by a pro who knows their way around a lens and a light meter.
What really sets it apart? The realism. The detail. The ability to take an idea and turn it into something that looks like it belongs in a magazine spread—or, in my case, a newsletter worth opening.
And here’s the kicker: It doesn’t just guess at what you want. It nails the vibe, the emotion, the scene. Whether it’s a dog in a business suit in Times Square or a surreal concept that lives only in your head, this image generator brings it to life with a kind of artistic intelligence I haven’t seen elsewhere.
Scroll down for a few examples I created using simple prompts (which are below the images). No photo-editing degree required. Just imagination—and ChatGPT.
Enjoy the future.

“Image of Hilary Clinton, Trump and Biden standing next to each other. Trump and Biden are holding boxes stuffed with papers. The outside of the boxes are marked classified, Clinton is holding a computer server marked classified. All of them look bemused.
In light of all the controversy surrounding phones. Here is my imagining of the future of conversation.

A caricature style illustration of A group of important and influential politicians and celebrities crowded around a table texting each other instead of talking. Label as "the future of conversation."
Let’s close on something Whimsical! Who doesn't love a Dog in a business suit?

A realistic photo of a close-up dog wearing a business suit in a crowd in Times Square looking at the camera and smiling, with the quality of one taken on a DSLR.
Appearance of the Week: Eric Sits down with the Secrets & Spies Podcast
I recently sat down with Chris Carr of the Podcast Secrets and Spies, and we discussed the takedown of one of the most dangerous traitors in American history: Robert Hanssen. We also explored how cybercrime exploded into a $12 trillion black-market economy, why deepfakes and ransomware are no longer sci-fi but real weapons, and how social engineering remains one of the biggest national security risks hiding in plain sight. If you’re curious how espionage tactics evolved into the cyber threats we now face daily, this is a conversation you don’t want to miss.
Like What You're Reading?
Don’t miss a newsletter! Subscribe to Spies, Lies & Cybercrime for our top espionage, cybercrime and security stories delivered right to your inbox. Always weekly, never intrusive, totally secure.
Are you protected?
Recently nearly 3 billion records containing all our sensitive data was exposed on the dark web for criminals, fraudsters and scammers to data mine for identity fraud. Was your social security number and birthdate exposed? Identity threat monitoring is now a must to protect yourself? Use this affiliate link to get up to 60% off of Aura’s Cybersecurity, Identity monitoring and threat detecting software!

Use this Link to get a 30 days trial + 2-% Beehiiv!

Ready for Next Week?
What do YOU want to learn about in my next newsletter? Reply to this email or comment on the web version, and I’ll include your question in next month’s issue!
Thank you for subscribing to Spies, Lies and Cybercrime. Please comment and share the newsletter. I look forward to helping you stay safe in the digital world.
Best,
Eric
Let's make sure my emails land straight in your inbox.
Gmail users: Move this email to your primary inbox
On your phone? Hit the 3 dots at top right corner, click "Move to" then "Primary."
On desktop? Close this email then drag and drop this email into the "Primary" tab near the top left of your screen
Apple mail users: Tap on our email address at the top of this email (next to "From:" on mobile) and click “Add to VIPs”
For everyone else: follow these instructions
Partner Disclosure: Please note that some of the links in this post are affiliate links, which means if you click on them and make a purchase, I may receive a small commission at no extra cost to you. This helps support my work and allows me to continue to provide valuable content. I only recommend products that I use and love. Thank you for your support!
