Last Chance to Register! Operation Book Launch
The countdown is on. October 7 marks the official launch of my new book, Spies, Lies, and Cybercrime. Consider this your invitation to the mission briefing at the International Spy Museum and sponsored by DeleteMe.
The launch event is running in person and online—so whether you’re reporting to HQ or tuning in from a safehouse, you can be part of it. Secure your clearance now.
Intel update: every week until launch, one lucky subscriber will win a free copy of the book. Entry is simple—stay subscribed and leave a comment on the newsletter. That’s all it takes to get your name on the list.
The winning Spy Hunter from Last week is: Patrick N. I’ll be sending you a free signed copy of Spies, Lies, and Cybercrime!
Agents, the mission is live. Don’t sit this one out.
In This Issue
Title Story: Descent Into the Dark Web: Beneath the Internet we trust lies a hidden world of crime, deception, and parasites feeding on our data.
Cybersecurity Breach of the Week: From car factories to airports, attacks prove that resilience—not just defense—is the only way to survive.
Cybersecurity Tip of the Week: Ransomware thrives on surprise. Backups, updates, and smart habits steal its advantage.
Appearance of the Week: This week, I appeared on Fox News to discuss the recent shooting at a Dallas Texas Ice Facility.
Closing Mission Brief: Join the October 7 launch of Spies, Lies, and Cybercrime—and don’t forget, subscribers who comment are entered to win a free copy every week.
Title Story
Descent Into the Dark Web
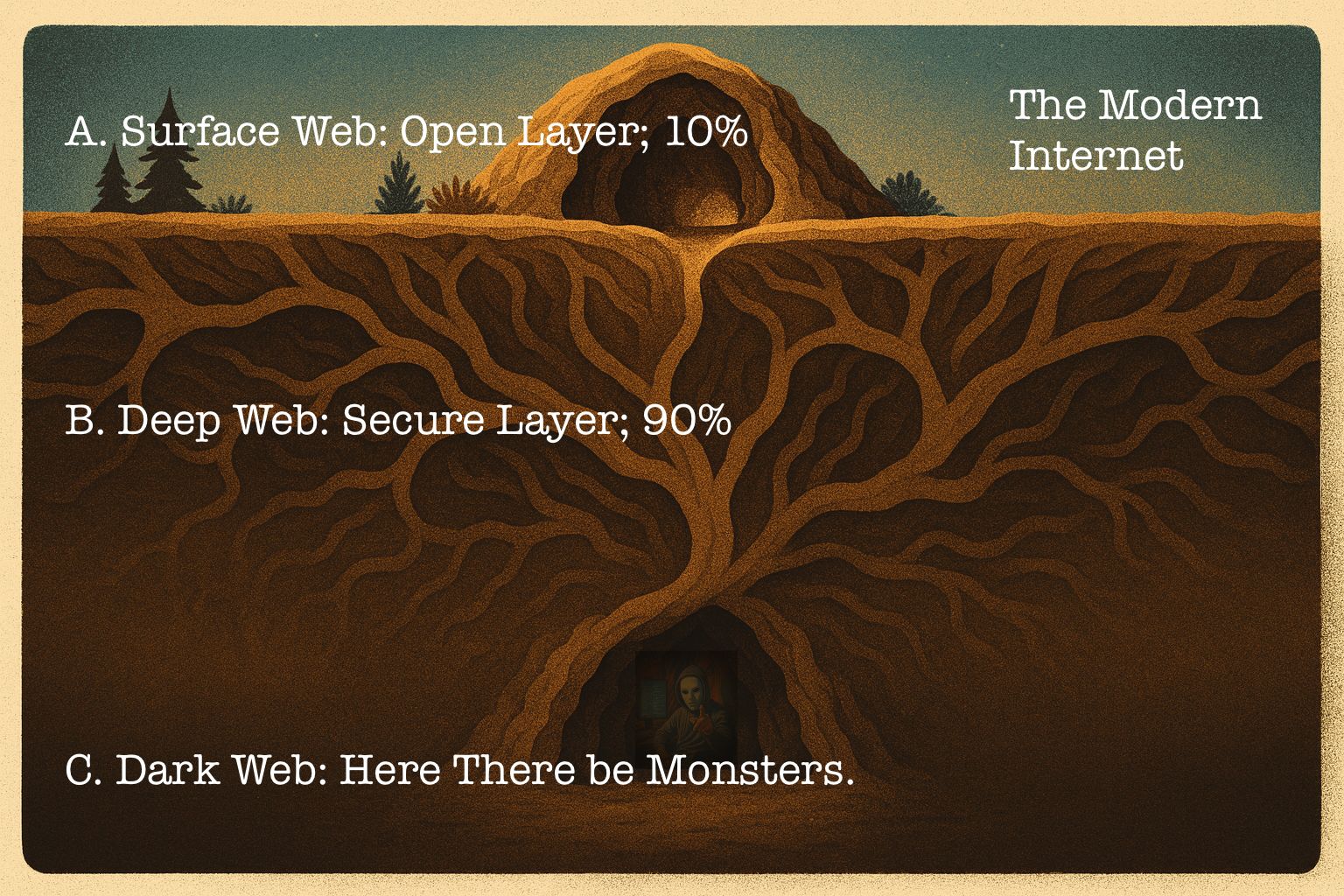
The Internet that lets you shop for groceries, stream a show, or pay your bill sits on a fragile crust. Beneath it, hidden in plain sight, sprawls a cavernous underworld built on anonymity, deception, and crime. It has a name: the Dark Web.
Only 10% of the nearly 180 zettabytes of data online is the Surface Web—the part we search, stream, and browse every day. Below lies the Deep Web, holding most of the world’s data behind passwords, firewalls, and multi-factor authentication. Here, a nonstop war rages between cyber defenders and criminals for the currency of our lives: information.
At the very bottom—just 5% of the Deep Web—lurks the Dark Web. It requires special browsers to access and provides a haven for cybercriminals who attack without fear of reprisal.
In my upcoming book, Spies, Lies, and Cybercrime (available October 7), I take readers down into those tunnels, where the digital floor drops away, shadows stretch forever, and, as the old maps warned, “here there be monsters.” Depravity at the touch of a button.
This may sound like Black Mirror. But it’s not fiction. It’s happening now. And it’s bleeding into everything we rely on.
The Rise of Cybercrime
Cybercrime already costs the world more than $13 trillion annually, and by 2026 it could reach $18-20 trillion. If the Dark Web were a nation, it would rank as the world’s third-largest economy—bigger than Germany and Japan combined.
But the greater crisis is trust. Within a year, AI-generated attacks will be indistinguishable from reality. Voices, videos, and texts—synthetic and convincing—will make every call, meeting, or transaction suspect. Trust, once the foundation of human interaction, will become uncommon.
What the Dark Web Really Is
Forget the caricature of hoodie-wearing loners in basements. The Dark Web isn’t a lone wolf with Wi-Fi. It’s a global ecosystem. Hidden, anonymized servers link criminals and spies who trade stolen data, franchise ransomware, and launder mountains of cryptocurrency.
It’s a marketplace. It’s a training ground. It’s a weapon.
And it thrives because we feed it. The more we live, work, and play online, the stronger its grip grows. The pandemic only accelerated it. While children lost a year of learning, cybercriminals enrolled in Dark Web “e-learning” platforms, building new ransomware schemes. Supply chain hacks once pioneered by Russia and China are now franchised and sold to anyone with cash.
The Business of Crime

Cybercrime has matured into a corporate juggernaut. Syndicates borrow tactics from spies: impersonation, manipulation, and exploitation of trust. They scan social media to tailor scams, pose as friends when you’re vulnerable, promise investments that don’t exist, or tug at heartstrings with fake pleas for help. They cloak themselves in stolen identities, ransom sensitive data, and drain accounts dry.
These aren’t petty thieves. They are professionalized, organized, and emboldened by the anonymity of the Dark Web. The fallout is everywhere: ransomware that cripples hospitals, fraud that devastates families, and coordinated campaigns that undermine nations.
To make the world safe from cyberattacks, we need more spy hunters. And that is exactly what this newsletter community is about. The more we understand the threat, the less likely we are to be deceived into handing over our data and wallets.
Knowledge is our weapon. Awareness is our armor. Together, we’re building a network of modern spy hunters who refuse to let the monsters of the Dark Web win.
Welcome to the hunt.
Cybersecurity Breach of the Week
From Dark Web to Real-World Mayhem
Last month, attackers forced Jaguar Land Rover to power down systems, silencing production lines across the U.K. Normally, those plants roll out about 1,000 vehicles a day. Each lost shift cost millions, rippling across Europe as suppliers were forced to scale back. The culprits? ShinyHunters a dark web cybercrime syndicate that breached AT&T Wireless in 2021 and again in 2024, stealing and selling data on nearly 200 million customers, compromised education software vendor PowerSchool in December 2024 and launched voice-phishing attacks against Salesforce in June 2025. Experts at supply-chain sabotage, they’ve turned ransomware into a precision weapon.

Source: LandRover
And it didn’t stop with cars. A yet undisclosed attacker collapsed check-in systems at European airports from Brussels to Berlin after ransomware crippled a third-party provider. Passengers groaned as flights were delayed, attendants scribbled boarding passes by hand, and yet another aspect of critical infrastructure was paralyzed.
Both JLR and the airports had invested heavily in cybersecurity. JLR signed an £800 million deal to modernize IT and defenses. Airports rely on industrial-strength aviation software. But the lesson is clear: defenses alone aren’t enough.
Resilience is what matters—before the attack. Redundancy, segmentation, zero-trust networks, and disaster recovery plans that actually work. And even those aren’t enough without people willing to hunt threats, not just react to them.
Cybersecurity Tip of the Week
10 Ways to Protect Yourself from Ransomware
Ransomware is when hackers lock up your computer and demand money to get your files back. Here’s how to spot trouble early—and stop it before it starts:

Slow computer or strange pop-ups – could be early signs of malware. Don’t ignore them.
Weird file names or extensions – if your files suddenly look different, act fast.
Keep your software updated – updates patch holes hackers use to get in.
Install strong antivirus/antimalware – let it scan regularly, not just when you remember.
Don’t click unknown links or attachments – phishing emails are still the #1 way ransomware spreads.
Back up your files – use an external drive or a secure cloud service. If ransomware hits, you won’t lose everything.
Use strong, unique passwords – and a password manager to keep track of them.
Turn on multi-factor authentication (MFA) – even if your password is stolen, MFA adds a second lock.
Disconnect from Wi-Fi if attacked – cutting off the internet can stop ransomware from spreading.
Have a recovery plan – know who to call (IT help, your work, or a trusted pro) before disaster strikes.
Hackers want you unprepared. The more ready you are, the less power they have.
Appearance of the Week
Watch my recent appearance on Fox News.
The attack on the ICE facility in Dallas is part of a disturbing trend of ideologically motivated shooters who etch threats onto ammunition and target government sites. In this case, the shooter fired indiscriminately into a sally port, left a note meant to terrorize ICE agents, and had researched ICE-tracking apps and DHS facilities. Just two months ago, there was another ICE shooting in Prairieland, Texas, underscoring the growing risk. My focus is on how ICE can better protect its agents: hardening vulnerable areas, breaking predictable routines, training relentlessly, equipping lifesaving tools, and tightening intelligence and detection.
Closing Note
We’ll wrap this week on a high note. My new book, Spies, Lies, and Cybercrime, officially launches on October 7—and you’re invited to the celebration.
The launch will be both in person and virtual, so whether you can join me on-site or from your desk, you can be part of the event. You can register HERE.
And don’t forget—the promotion is still live. Every week, I’m giving away a copy of Spies, Lies, and Cybercrime to one lucky subscriber. Entering is simple: stay subscribed and leave a comment on the newsletter. That’s it. It’s my way of saying thanks for being part of this community as we head toward the book’s release. I can’t wait to share it with you.

Join 400,000+ executives and professionals who trust The AI Report for daily, practical AI updates.
Built for business—not engineers—this newsletter delivers expert prompts, real-world use cases, and decision-ready insights.
No hype. No jargon. Just results.
Like What You're Reading?
Don’t miss a newsletter! Subscribe to Spies, Lies & Cybercrime for our top espionage, cybercrime and security stories delivered right to your inbox. Always weekly, never intrusive, totally secure.
Are you protected?
Recently nearly 3 billion records containing all our sensitive data was exposed on the dark web for criminals, fraudsters and scammers to data mine for identity fraud. Was your social security number and birthdate exposed? Identity threat monitoring is now a must to protect yourself? Use this affiliate link to get up to 60% off of Aura’s Cybersecurity, Identity monitoring and threat detecting software!

Use this Link to get a 30 days trial + 2-% Beehiiv!

Ready for Next Week?
What do YOU want to learn about in my next newsletter? Reply to this email or comment on the web version, and I’ll include your question in next month’s issue!
Thank you for subscribing to Spies, Lies and Cybercrime. Please comment and share the newsletter. I look forward to helping you stay safe in the digital world.
Best,
Eric
Let's make sure my emails land straight in your inbox.
Gmail users: Move this email to your primary inbox
On your phone? Hit the 3 dots at top right corner, click "Move to" then "Primary."
On desktop? Close this email then drag and drop this email into the "Primary" tab near the top left of your screen
Apple mail users: Tap on our email address at the top of this email (next to "From:" on mobile) and click “Add to VIPs”
For everyone else: follow these instructions
Partner Disclosure: Please note that some of the links in this post are affiliate links, which means if you click on them and make a purchase, I may receive a small commission at no extra cost to you. This helps support my work and allows me to continue to provide valuable content. I only recommend products that I use and love. Thank you for your support!



