The Holidays are Here!
Ever feel like you need a vacation to recover from a vacation? Thanksgiving left me feeling that way, but in a good way! I disconnected from technology, spent time with family, ate too much and spent a bitterly cold day outside cheering for the Washington Commanders in a big group with all my children and assorted friends. Now that it back to work, I could use a few more days of just resting and recovering. But it’s Tuesday, and that means another exciting issue of Spies, Lies & Cybercrime.
This week I’m continuing a series I began on surviving holiday scams. Cyber criminals are firing on all cylinders this holiday season. Scams are already at their highest levels and I’ve joined countless TV, podcast and media to get the word out about the many, devious and corrupt ways the bad guys pull on your heartstrings and invade your wallet.
Something the Johnson family learned the hard way!
The Heartstrings Scam: When Kindness Meets Deception
Every January, the Johnson family gathered for their favorite tradition: choosing a cause to support with their annual donation. Around the dining table, they’d reflect on the past year, share what they were grateful for, and decide together how they could make the world a better place.
This year, the decision wasn’t difficult. Hurricane Helene had ravaged parts of North Carolina and Florida, leaving entire communities in ruins. Photos of children standing in front of collapsed homes were heart-wrenching. Emma, the ever-thoughtful 14-year-old, spoke first. “We should help them,” she said.

Her mom, Sarah, nodded. “I read about families sleeping in cars because their houses were destroyed. What if we donated to help rebuild their homes?”
“That sounds perfect,” said Emma’s father Tom. He prided himself on teaching his kids the importance of giving back.
Even 10-year-old Jack was on board. “Let’s do it! Can we send the money now, Dad?”
Little did the Johnsons know, their goodwill was about to make them the perfect targets for a sophisticated scam.
The Perfect Hook
Later that evening, as Sarah watched the evening news while Tom idly scrolled through his email, Tom paused when a message caught his eye: “Urgent: Help Save Children Left Homeless by Hurricane Helene!” The email was from a group calling itself the Helene Disaster Relief Fund.
“Hey, Sarah, look at this,” Tom said, opening the email. The message was filled with compelling images: entire neighborhoods reduced to rubble, children clutching teddy bears in front of collapsed homes, and glowing testimonials from families whose lives had been “restored.”
“Your donation can make the difference between despair and hope,” the email urged. “Please act now. Every second counts.”
As Tom and Sarah scrolled through the email, his phone buzzed again—this time with a text message.
“Tom, we noticed you didn’t complete your donation to Helene Disaster Relief. Please click here to save a child today.”
“That’s weird,” Sarah said. “How do they know your name?”
Tom shrugged. “Maybe they pulled it from a mailing list? It’s kind of creepy, but the website looks legitimate.”
Emma wandered into the room. “Is that the charity we’re donating to?” she asked, peeking at the screen.
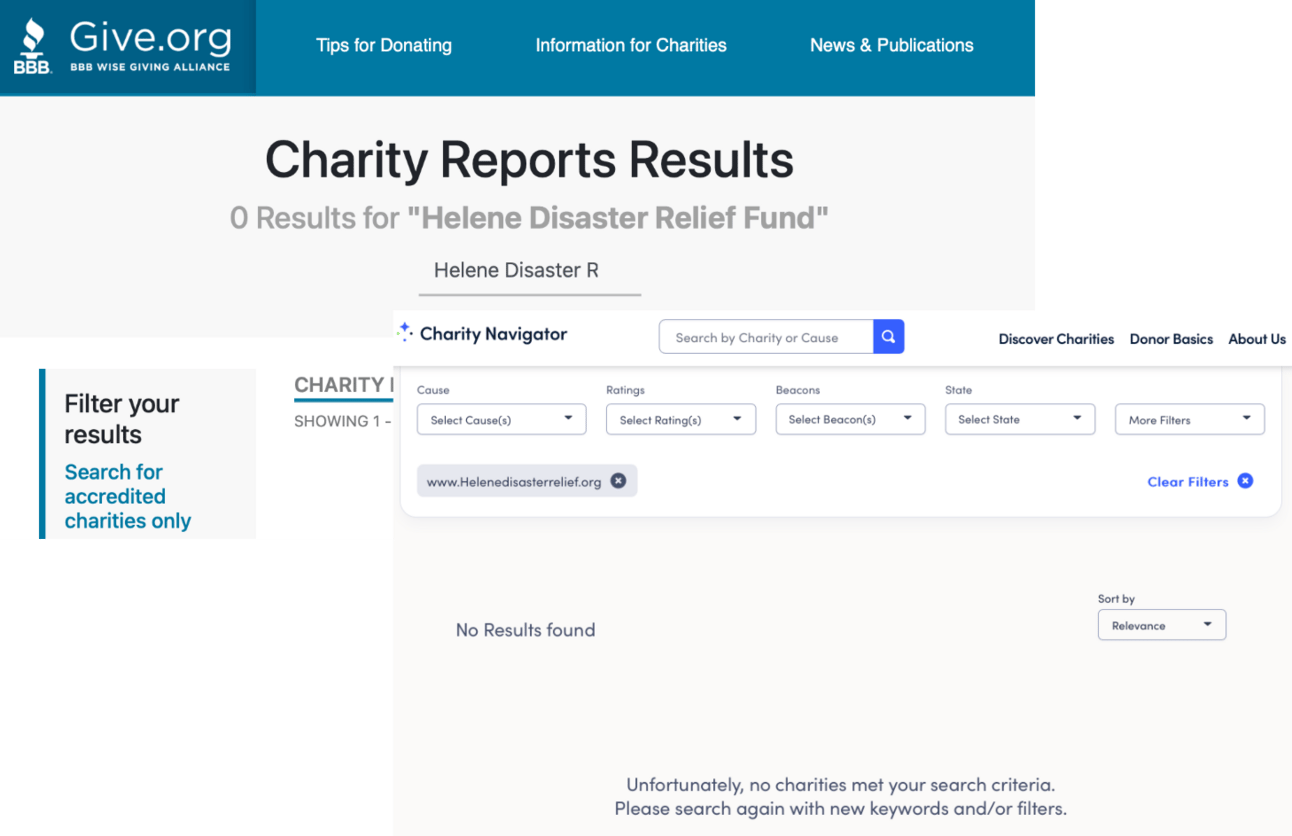
Tom clicked the link, which took him to a website: www.Helenedisasterrelief.org. The site looked polished and professional, with more photos of devastation and glowing testimonials from “beneficiaries.” The donation form was simple and looked secure.
“It’s for a good cause,” Sarah said. “Let’s just do it.”
Tom entered their credit card details and hit “Donate.” A confirmation email immediately arrived, thanking them for their $5,000 contribution. The Johnsons felt proud—they had done their part to help families rebuild.
The Truth Comes Out
Months later, as tax season approached, Sarah reminded Tom to request a donation receipt from the Helene Disaster Relief Fund. “We’ll need it for our taxes,” she said.
Tom fired off a quick email to the address listed in the confirmation message. Days passed with no response. Growing suspicious, he revisited the website—but it was gone. The URL now led to an error page.
“What’s going on?” Sarah asked.
Tom frowned and searched online for the organization. There were no results. No articles, no reviews, no record of Helene Disaster Relief ever existing. That’s when he noticed something else: the email had come from Helenedisasterrelief.org, not .com or .gov, as he might have expected.
“Did we get scammed?” Sarah asked, her voice tight with worry.
Tom’s stomach dropped. “I think so.”
The Investigation
Determined to get answers, Tom and Sarah contacted a cybersecurity investigator. What they uncovered was chilling.
The email and text messages had been part of a highly targeted phishing campaign. Using publicly available data, the scammers had crafted messages tailored to people likely to donate to disaster relief efforts. The website was a near-perfect replica of a legitimate charity site, complete with AI-generated photos and glowing testimonials.
Their donation had gone into a drop account, which was emptied within hours. The funds were converted to cryptocurrency, laundered through multiple wallets, and disappeared into the dark web.
There was no way to recover the $5,000.
Breaking the news to Emma and Jack was the hardest part. “But Mom,” Jack protested, “we were trying to help people. Why would anyone do this?”
Sarah sighed. “Because some people only care about taking advantage of others,” she said. “But we’ll learn from this, and we’ll make sure it doesn’t happen again.”
Lessons Learned
The Johnsons’ experience is a cautionary tale, but it’s one that others can learn from. Charity scams spike during disasters and the holiday season, preying on people’s emotions and goodwill.
Here’s how to protect yourself:
Be Wary of Unsolicited Messages: Legitimate charities rarely send urgent, personalized requests via email or text. If you receive one, proceed with caution.
Verify Before You Donate: Research the charity’s name and web address using trusted sites like Charity Navigator or the Better Business Bureau’s Wise Giving Alliance.
Check the URL: Scammers often create web addresses with slight misspellings or unusual domain extensions. Always triple-check the URL before donating.
Don’t Click Links: Instead of clicking on links in emails or texts, type the charity’s official URL directly into your browser.
Ask Questions: Real charities are transparent about how donations are used. If an organization is evasive or pressures you, walk away.
The holiday season is a time for generosity, but it’s also a time for vigilance. Scammers thrive on urgency and emotion, knowing how to exploit your kindness for their gain.
Now on to the news!
News Roundup
Scammers Love to Deepfake Elon Musk with AI
AI is revolutionizing industries, but it’s also fueling a deepfake fraud epidemic set to skyrocket to $40 billion in losses by 2027. Scammers are leveraging hyper-realistic deepfakes of familiar faces (like Elon Musk) to con victims with cloned voices and videos that are shockingly convincing. The takeaway? Trust is the real casualty here—stay vigilant, verify everything, and remember that in the age of AI, seeing isn’t always believing.
Sneaky Criminal
An IT manager at a Connecticut gun shop turned off the cameras, raided the safe, and methodically embezzled over $2 million in cash across eight years—then turned the cameras back on, prosecutors revealed. Evan Bobzin used the stolen funds for personal expenses and dodged taxes, leaving his former employer, Scott Hoffman, stunned and devastated by the betrayal of a trusted friend. Now sentenced to two years in prison and ordered to repay every cent, Bobzin has tarnished reputations, strained relationships, and left a trail of broken trust that no restitution can fully repair.
The $760 Million Decluttering Mistake
James Howells, the man behind one of the most expensive tech blunders in history, has a new twist to his story: his $760 million worth of Bitcoin was accidentally trashed by his ex—but at his request. Halfina Eddy-Evans revealed she was simply helping Howells clean up when she unknowingly discarded the hard drive containing 8,000 Bitcoin. While she hopes he can recover it, this epic mistake serves as a pricey reminder to double-check what’s in the bag before it hits the trash.
Chinese Telecom Espionage
Chinese state-sponsored hackers, known as "Salt Typhoon," breached T-Mobile's routers in a failed attempt to explore its network for further exploits. T-Mobile's proactive defenses, including monitoring and network segmentation, stopped the attack before any sensitive customer data or services were compromised. While other telecom giants like AT&T and Verizon reportedly suffered long-term breaches, T-Mobile's swift action prevented the hackers from gaining access to calls, texts, or customer information, showcasing the importance of robust cybersecurity measures in fending off advanced threats.
Another Background Check Breach Exposes Over 600,000 Records
It’s happened again. SL Data Services, a background check company, suffered a breach exposing sensitive data from over 600,000 people. This marks the second major incident of its kind, following the massive CDK breach earlier this year. The unprotected database contained over 700GB of files, including names, addresses, court records, employment details, and more, all labeled as “background checks.” Although Social Security numbers and payment data weren’t included (this time), the volume of personal information could fuel social engineering attacks.
Holiday Tech of the Month
Tired of the same old yule log crackling away on your TV during holiday parties? NASA has taken the virtual fireplace to the next level—literally rocket-level—with an 8-hour, 4K "Rocket Engine Fireplace." Featuring the glow and roar of the SLS rocket’s four RS-25 engines, this unique holiday vibe packs enough "heat" to get you to the Moon (or just through awkward family conversations).
Decked out with framed pics of the Artemis mission and the Orion capsule, it’s perfect for space enthusiasts or anyone who wants their holiday gatherings to blast off. Bonus: no chimney required—just crank up the thermostat and let this cosmic crackler “ignite” your party. It’s festive, it’s fiery, and it’s guaranteed to blow your guests away (figuratively, of course). [Click the Watch on YouTube logo]
Check out my latest News appearance
I recently sat down with NBC Louisville to discuss holiday scams and the actions we can all take to stop fraudsters before they play on our heartstrings and steal our wallets. [Click the Watch on YouTube logo]
Like What You're Reading?
Sign up for Spies, Lies & Cybercrime newsletter for our top espionage, cybercrime and security stories delivered right to your inbox. Always weekly, never intrusive!
Are you protected?
Recently nearly 3 billion records containing all our sensitive data was exposed on the dark web for criminals, fraudsters and scammers to data mine for identity fraud. Was your social security number and birthdate exposed? Identity threat monitoring is now a must to protect yourself? Use this link to get up to 60% off of Aura’s threat monitoring service.
What do YOU want to learn about in my next newsletter? Reply to this email or comment on the web version, and I’ll include your question in next month’s issue!
Thank you for subscribing to Spies, Lies and Cybercrime. Please comment and share the newsletter. I look forward to helping you stay safe in the digital world.
Best,
Eric
Let's make sure my emails land straight in your inbox.
Gmail users: Move this email to your primary inbox
On your phone? Hit the 3 dots at top right corner, click "Move to" then "Primary."
On desktop? Close this email then drag and drop this email into the "Primary" tab near the top left of your screen
Apple mail users: Tap on our email address at the top of this email (next to "From:" on mobile) and click “Add to VIPs”
For everyone else: follow these instructions

